As mentioned in other articles, Tidecoin mining algorithm is ASIC’s neutral and gpu unfriendly. Therefore, private devices can be used excellently to mine the coin.
Tidecoin offers two solutions that do not require IT expertise, the webminer and a mining app for Android.
Webminer
The Weminer can be accessed via the following URL. Your public key address to which the Coins are to be paid out must be inserted after “/workers/”.
https://pool.tidecoin.exchange/workers/YOUR_WORKER_ADDRESS
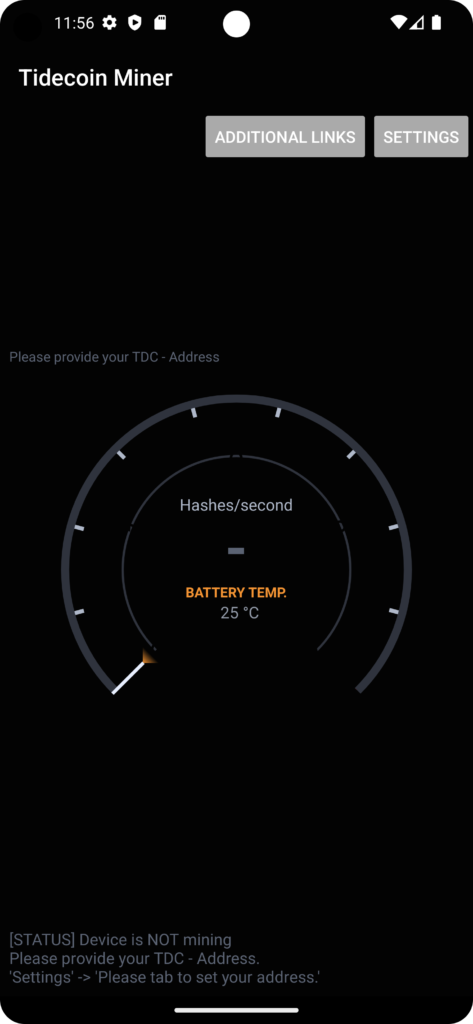
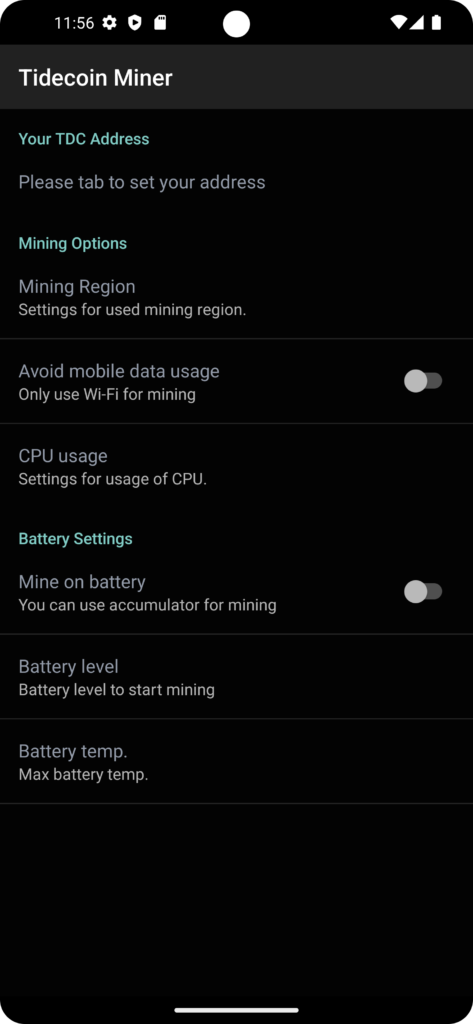
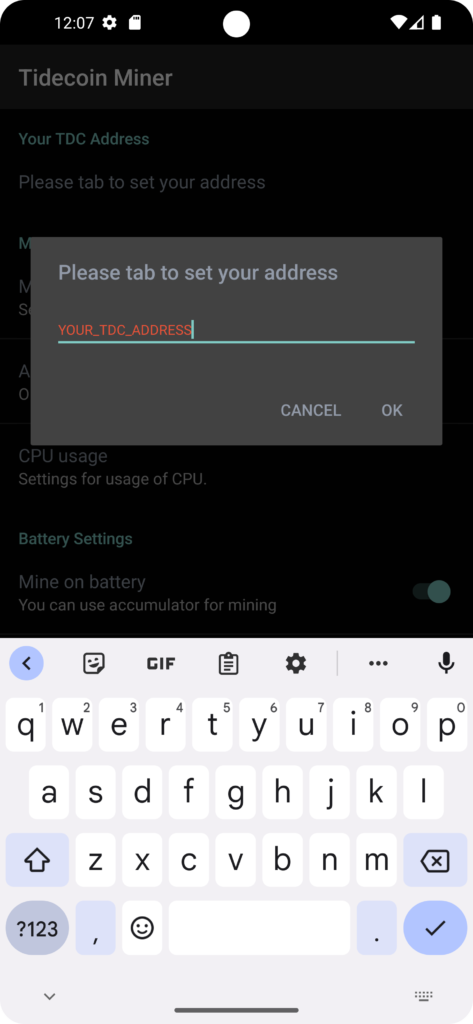
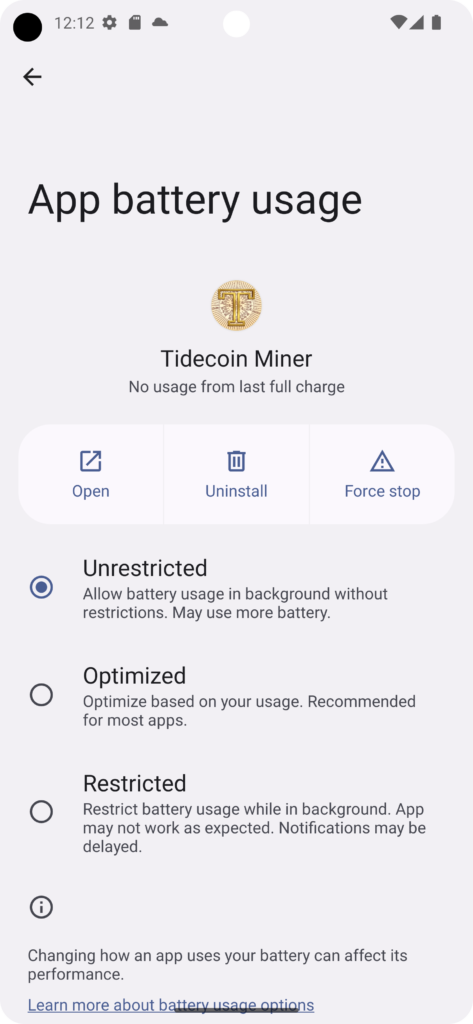
MOBILE Miner
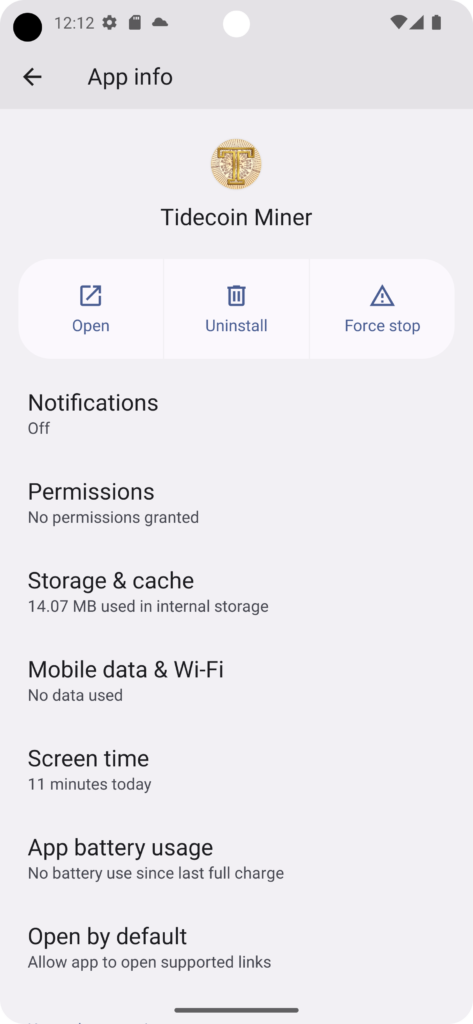
A mobile miner was developed for Android devices. The apk can be downloaded from the following URL. The mining starts automatically when the conditions are met, which are stored under the settings, even if display is locked. For example your device will mine Tidecoin for you, if you are charging your device. Please give the app the rights for background activities, foreground activities and automatic start in the battery settings. The settings should be found under “Power Consumption Control” or Battery Consumption. Long press on the app icon -> “App info” -> “Battery usage”.