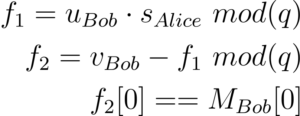This article should give a short example, how lattice based encryptions are working.
Following parameters are given. n is the number of matrixes, which are choosen. k is the dimension of every matrix and q must be a prime number, to limit the size of fields.
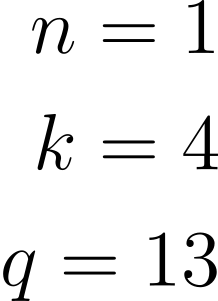
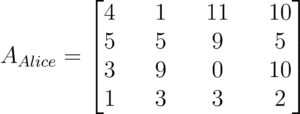
Alice will choose a Matrix A. This is her public key.
She will also choose here secret key s.
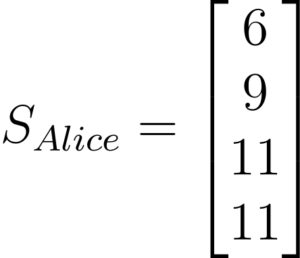
Now Alice will choose a random vector e.
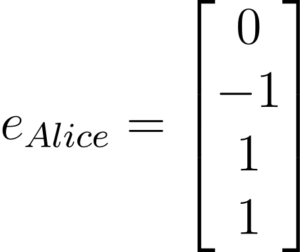
Alice will calculate t with her public key A, her secret key S and her random vector e.
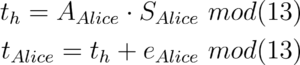
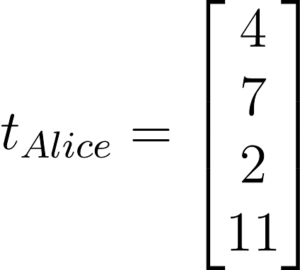
Bob will receive A and t from Alice.
Bob will choose a random vector r, e1, e2 and he will select the message M he like to send.
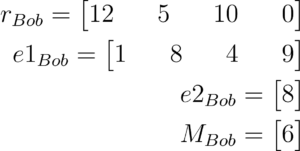
Bob will now calculate an encryption and a kind of helper encryption output for Alice.
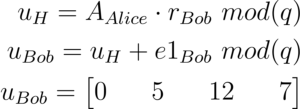
Now Bob will calculate his secret message.
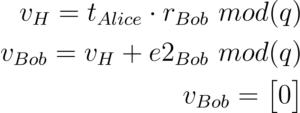
Alice will decript the message with using u and v from Bob and her private key s.